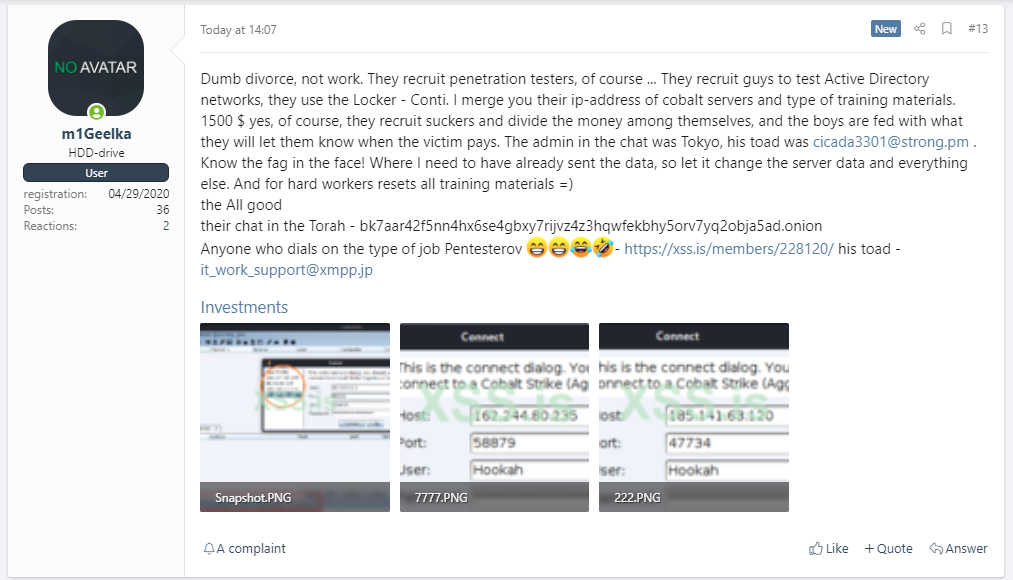
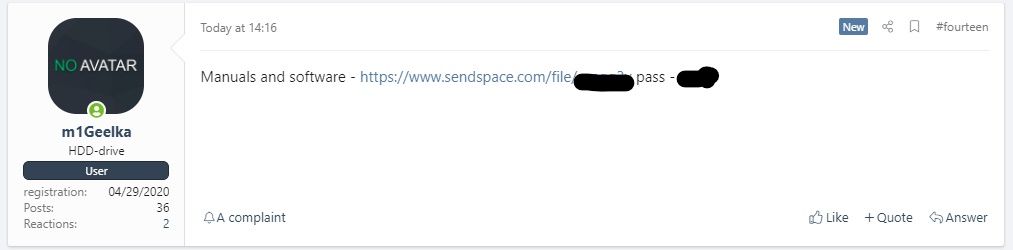
On 5 August 2021, a forum user identified as m1Geelka, leaked an archive of the Conti gang's manual and technical guides in the hacking forum XSS.is. It seemed that the user was an affiliate to Conti Gang and leaked the files due to a salary dispute.
Conti Ransomware Gang
- First discovered in December 2019, and started operating as a personal ransomware-as-a-service (RaaS) model in July 2020.
- Likely to be operated with the same operators that conducted
Ryukransomware attacks in the past (source: CarbonBlack). - Victims are high value targets in many Medical sectors (U.S. Health Emergency Networks, Ireland Health Service Executive)
- Recorded Techniques from MITRE ATT&CK.
Leaked files at a glance
The leaked archive was titled, Мануали для работяг и софт.rar (roughly translated to Manuals for hard workers and software.rar) and contains 51 files in total. The archive included instructions to use a range of applications to aid in their attacks such as net scanners, proxifiers,RDP software, configuring and using Cobalt Strike, how to perform privilege escalation, how to dump credentials, how to perform brute-forcing, using ZeroLogon or Kerberoasting, deleting shadow copies, performing data exfiltration, and more.
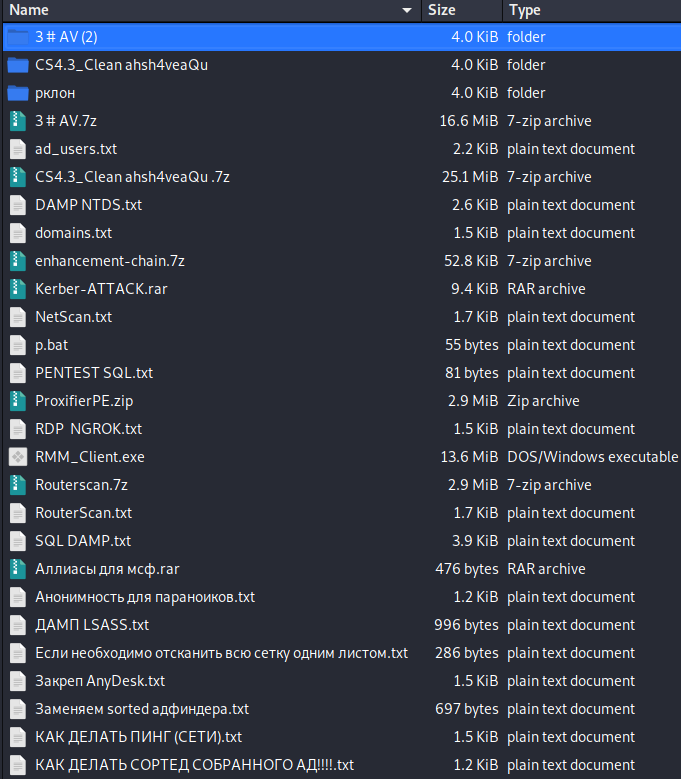
Certain archives are password protected but the community had managed to crack them.
| Original Filename | Translated Filename | Remarks |
|---|---|---|
| AV.7z | AV.7z | Contains scripts to help disable AV |
| ad_users.txt | ad_users.txt | Instructions to hunt for specific users using Powerview. |
| CS4.3_Clean ahsh4veaQu .7z | CS4.3_Clean ahsh4veaQu .7z | Cobalt Strike builds |
| DAMP NTDS.txt | DAMP NTDS.txt | Instructions to dump Windows NT Directory Services (NTDS) |
| domains.txt | domains.txt | List of hostnames |
| enhancement-chain.7z | enhancement-chain.7z | Set of Cobalt Strike scripts written by mgeeky. Comes with a custom README |
| Kerber-ATTACK.rar | Kerber-ATTACK.rar | Steps to perform Kerberoasting |
| NetScan.txt | NetScan.txt | Instructions to use NetScan software |
| p.bat | p.bat | Ping to hosts listed in domains.txt |
| PENTEST SQL.txt | PENTEST SQL.txt | link to PowerUpSQL |
| ProxifierPE.zip | ProxifierPE.zip | Proxy tool to route network traffic |
| RDP NGROK.txt | RDP NGROK.txt | Instructions to setup NGROK to perform secure RDP |
| RMM_Client.exe | RMM_Client.exe | Remote Monitoring and Management Client |
| Routerscan.7z | Routerscan.7z | Contains RouterScan by Stas'M |
| RouterScan.txt | RouterScan.txt | Instructions to use RouterScan to scan and identify routers, internet cameras and attempt to bruteforce exploit to gain access |
| SQL DAMP.txt | SQL DAMP.txt | SQL queries to query specific SQL data |
| Аллиасы для мсф.rar | Alliases for msf.rar | Assign alias for metasploit modules |
| Анонимность для параноиков.txt | Anonymity for the paranoid.txt | Advices from Conti Gang for its 'paranoid' operators in staying anonymous |
| ДАМП LSASS.txt | DUMP LSASS.txt | Methods to dump LSASS |
| Если необходимо отсканить всю сетку одним листом.txt | If you need to scan the entire grid in one sheet. Txt | Instructions to use AdFind to enumerate the internal network |
| Закреп AnyDesk.txt | Fix AnyDesk.txt | Instructions to download and install AnyDesk on victim as a form of persistency |
| Заменяем sorted адфиндера.txt | Replace sorted adfinder.txt | Seems to be adding and running a Cobalt Strike Beacon in Scheduled Tasks |
| КАК ДЕЛАТЬ ПИНГ (СЕТИ).txt | HOW TO PING (NETWORK) .txt | Instructions to create custom domains.txt that stores a list of hostnames/domains and using p.bat to execute ping against domains.txt. |
| КАК ДЕЛАТЬ СОРТЕД СОБРАННОГО АД!!!!.txt | HOW TO MAKE SORT OF COLLECTED HELL !!!!. Txt | Instructions to setup tor network and Filezilla for data exfiltration purposes |
| КАК И КАКУЮ ИНФУ КАЧАТЬ.txt | HOW AND WHAT INFO TO DOWNLOAD.txt | Instructions on common files to look for and how to exfiltrate them using Rclone. |
| КАК ПРЫГАТЬ ПО СЕССИЯМ С ПОМОЩЬЮ ПЕЙЛОАД.txt | HOW TO JUMP SESSIONS USING PAYLOAD.txt | Seems like instructions to send the established session to Cobalt Strike. |
| Личная безопасность.txt | Personal Safety.txt | Instructions for operators to encrypt their VM storage using VeraCrypt before using it for their operations. |
| МАНУАЛ.txt | MANUAL.txt | Instructions to perform discovery and enumeration |
| Мануал робота с AD DC.txt | Robot manual with AD DC.txt | A set of instructions to perform discovery and enumeration with open source tools and scripts |
| Меняем RDP порт.txt | Change RDP port.txt | Commands to change RDP ports |
| ОТКЛЮЧЕНИЕ ДЕФЕНДЕРА ВРУЧНУЮ.txt | DISABLING THE DEFENDER MANUALLY.txt | Instructions to disable WinDefender |
| параметр запуска локера на линукс версиях.txt | locker launch parameter on linux versions.txt | Usage of Locker malware (?) on linux systems |
| ПЕРВОНАЧАЛЬНЫЕ ДЕЙСТВИЯ.txt | INITIAL STEPS.txt | Lists steps to take when after getting initial access |
| ПОВИЩЕНИЯ ПРИВИЛЕГИЙ.txt | VENTURE OF PRIVILEGES.txt | Link to repository for AD exploitation |
| поднятие прав (дефолт).txt | elevation of rights (default) .txt | Instructions to escalate privileges using Cobalt Strike(similar to msf's getsystem) |
| Получение доступа к серверу с бекапами Shadow Protect SPX (StorageCraft).txt | Gaining access to the server with backups Shadow Protect SPX (StorageCraft) .txt | Instructions to gain access to victim backups using Shadow Protect SPX by StorageCraft |
| по отключению дефендера.txt | to disable defender.txt | Another set of method to disable WinDefender |
| ПРОСТАВЛЕНИЕ.txt | PROSTITION.txt | Commands to copy/run file as Domain Admin using PsExec or WMIC |
| Рабочая станция на работу через Tor сетїь.txt | Workstation to work through the Tor network.txt | Instructions to have the operators' workstations to tunnel Through Tor network. |
| Рабочий скрипт создания VPS сервера для тестирования на проникноваение от A до Z.txt | Working script for creating a VPS server for penetration testing from A to Z.txt | Link to tutorial to setup a Virtual Private Server |
| рклон.zip | rclone.zip | Rclone executable and configuration instructions |
| Сайт создание батникоd.txt | Website creation batnikod.txt | A link to a strings formatter |
| Скрипт для sorted .rar | Script for sorted .rar | Script to map ad_users to ad_computers. |
| СМБ АВТОБРУТ.txt | SMB AUTOBRUT.txt | Instructions to bruteforce passwords using Cobalt Strike |
| СНЯТИЕ-AD.rar | REMOVAL-AD.rar | AdFind executable and set of default commands to use for enumeration |
| Список ТГ форумов, много интересного.txt | List of TG forums, many interesting things.txt | List of interesting Telegram Groups for hacking |
| Установка метасплойт на впс.txt | Installing metasploit on vps.txt | Instructions to install MSF on VPS |
| хантинг админов, прошу ознакомиться, очень полезно!!.txt | hunting admins, please read, very useful !!. txt | Instructions on how to hunt for admins in the network. (The text contained french on top of russian.. interesting..) |
| Эксплуатация CVE-2020-1472 Zerologon в Cobalt Strike.txt | Exploiting CVE-2020-1472 Zerologon at Cobalt Strike.txt | Instructions to use ZeroLogon exploit in Cobalt Strike. |
| это установка армитажа. ставится поверх Metasploit | this is an armitage installation. put on top of Metasploit | Instructions to install Armitage |
Cobalt Strike Manuals V2
In other articles, there seemed to be a manual included which I wasn't able to find in the archive I obtained. However, the people from OALabs translated the manual and streamed their discussion live.
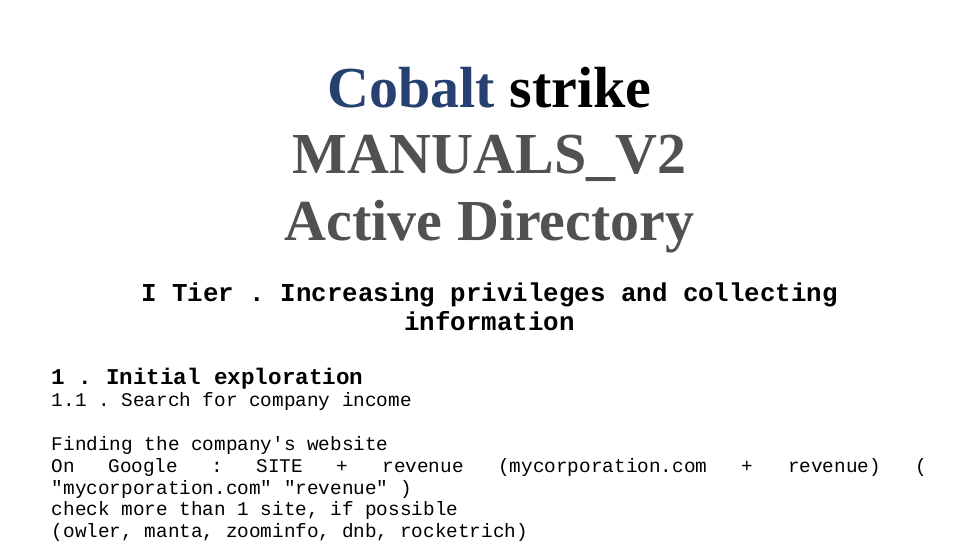
The manual records the Conti Gang's TTP on their victims, beginning from selecting their targets. The manual does not include how they get their targets to fall for their attack, but it is likely SpearPhishing, based on other reports. Some terms that frequently appeared whilst going through the data were the terms wheelbarrow and ball. Inferring from context, it seems that wheelbarrow translates to shell/cmd and ball translates to file share\ directory.
For technical analysis on Conti Gang's past attacks, you may visit MITRE ATT&CK, Carbon Black, DFIR, Sophos and Cybereason.
Conclusion
Keeping an organisation's data secure comes from multiple angles. Users should practice good cyber hygiene such as proper data handling, adhering to strong password practices, etc. And the organisation should lay policies and rules to enforce these practices. But of course, the dilemma is balancing productivity/ efficiency against security. However, is an organisation really ready to accept the risk?

