With a long weekend ahead, I decided to gather a few friends and formed a team to participate in the DEFCON 29 RTV CTF. We came in with one goal in mind, to have fun. What I've covered in this 2-part post are only challenges that I attempted.
These are the challenges recorded in this part 1 of 2 post:
- Ancient Crypto Corner - The name's Caesar
- Cracking - Easy Crack 1 to 5
- Network Forensics - Protected OSPF
- FLAGUSB - Look at what Wireshark can do!
Challenge Start
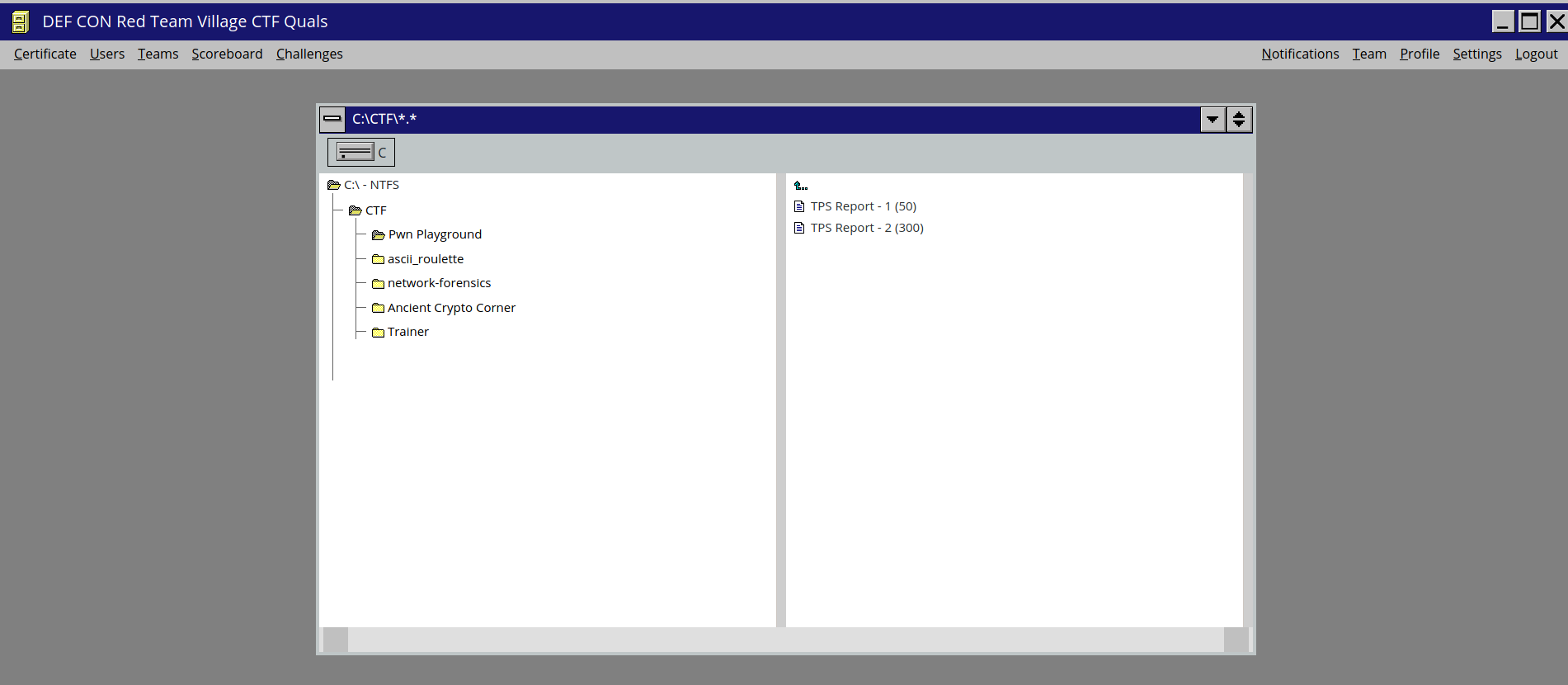
The event challenge was released at 10AM (UTC) and these were the challenges.
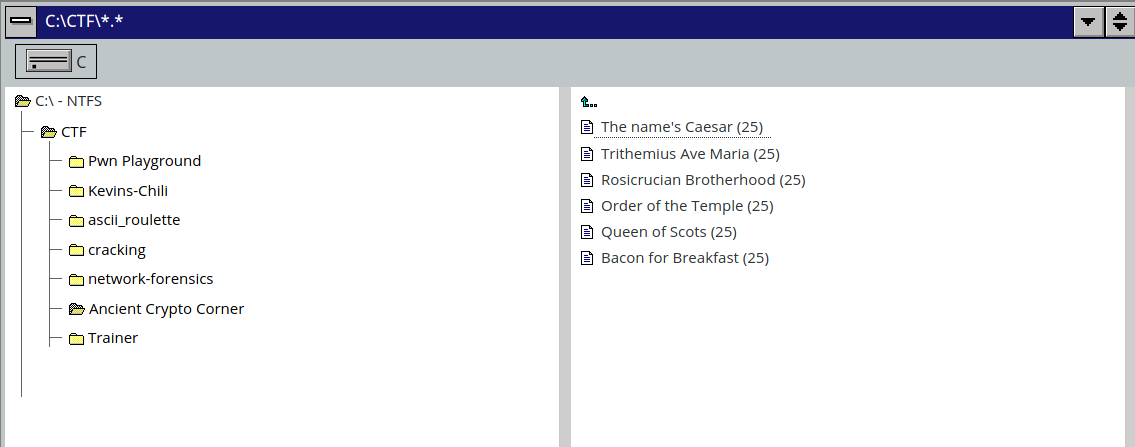
More challenges were added along the way, and my friends and I went ahead to do what was available. Because all we wanted to do was have fun, so we just did what we found interesting.
The name's Caesar (Caesar Cipher)
I first started with the Caesar Cipher(I like a salad before my entrée) challenge named The name's Caesar, under the Ancient Crypto Corner category.
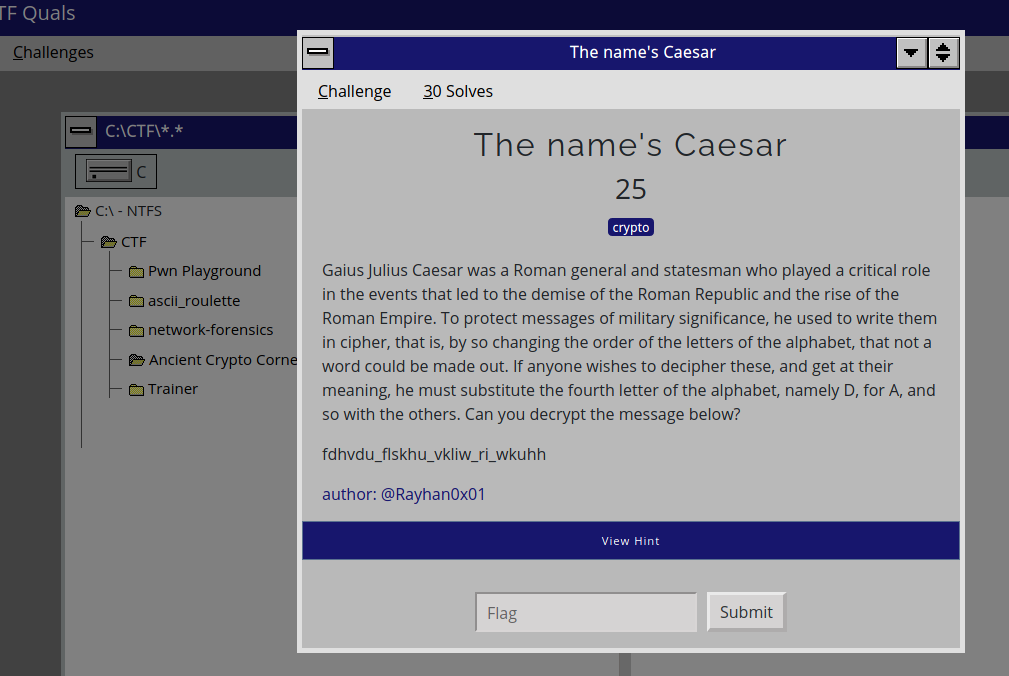
Caesar Cipher is a form of shift cipher where a key would be pre-determined between senders/receivers so that either would know what each letter in the coded message actually represents. Read more here.
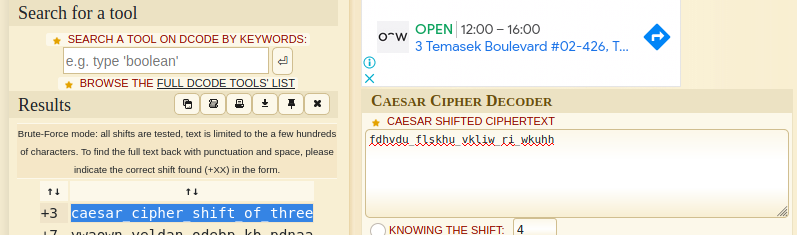
I used a public decoder and got the flag caesar_cipher_shift_of_three. The +3 indicated the key shift was at 3.
Easy Crack 1-5 (Hash cracking)
The next challenge I picked were challenges easy crack 1 to 5.
Easy Crack 1 and 5 were MD5 hashes which could was easily cracked when I looked up crackstation.


Easy Crack 2,3 and 4 were luckily also found in wordlist after identifying the right type of hash.
I used hashcat to identify the hash by recognising the pattern against hashcat example hashes.
hashcat --example-hashes | grep "\$6\$*" -B 4
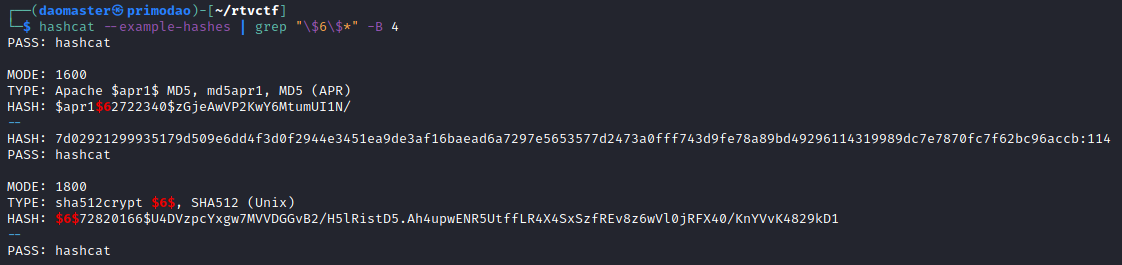
Knowing the mode to select, I ran hashcat on the hashes (I saved all the hashes in a file called easycracks) against rockyou.txt to crack the hashes.
hashcat -m 1800 -a 0 easycracks /usr/share/wordlists/rockyou.txt
and after approximately 40-45 minutes, the hashes were cracked.
Christopher:$6$33VlMNJ9o4Xyi343$.1edgNlimWliqoXi2ETLEM4qQk7U.sYo2gCeqs9HlZMlvJGnibSP.BCw4cdpGUqE41Bxjp.fWI2iDKClGBxoR1 (2316AY)
Sean:$6$MPCZQ37FAGshRIep$W1lDSSonF8P080J/VmsS2QVsbkCGPVxcjomFiGTHsWrgS8wBOBWgYonUciXbpY/LmIxnKNX/j4lsuRFegZhFE0 (moe512)
Jessica:$6$qUX8cPJFtK0MIJqG$pFW1bnU4qaS8O9lv1gfsG3/CCa7F2SS12m5ivkrGVO7/Sqtd2/c.RR52d5WQ2461ZbTnOMh7zzGJoXZRO5/rP/ (shikari90)
For these challenges, the cracked hashes were the flag.
Cracking OSPF passphrase (Protected OSPF)
The next one was in the network forensics category named Protected OSPF.
The file for this challenge was a .pcap file, which contained a MD5 sum of the passphrase used to secure the OSPF routing protocol.
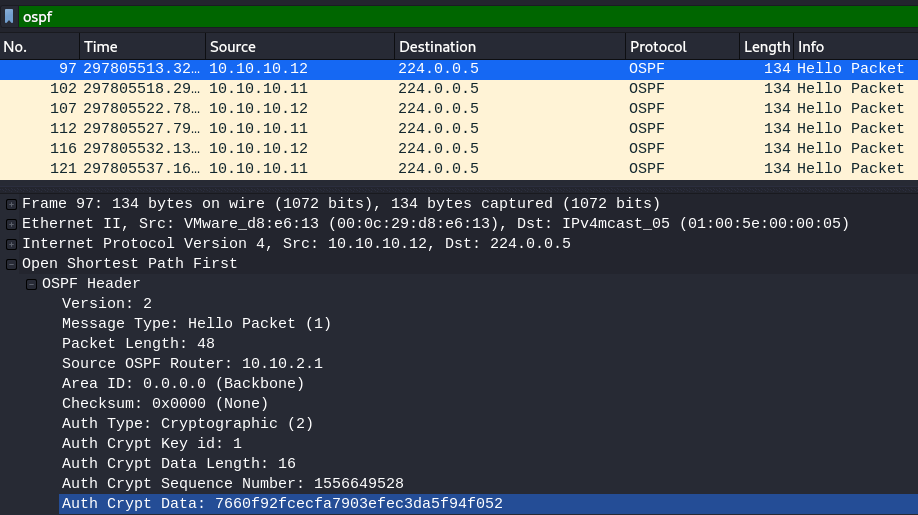
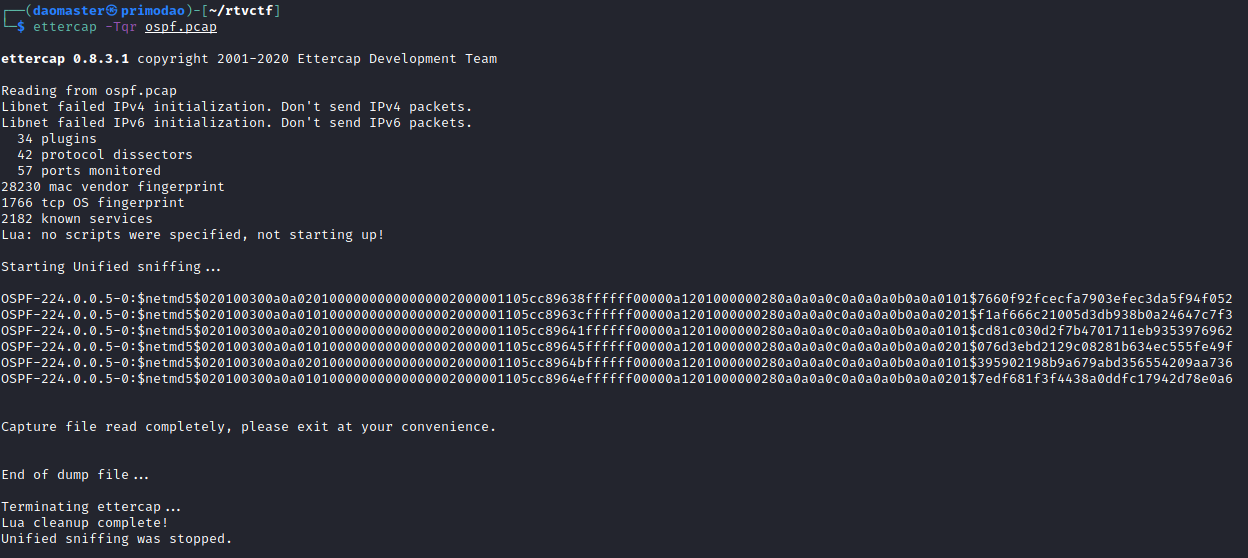
During this CTF, I learnt that ettercap is able to extract certain network protocol (e.g. OSPF, RIPv2) password hashes and convert the format for JohnTheRipper (JtR).
ettercap -Tqr ospf.pcap
T: Text-only
q: quiet
r: read file
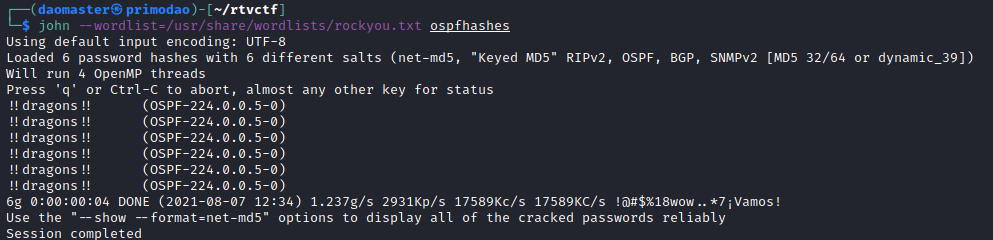
With the extracted hashes, I ran JtR with the hashes against rockyou.txt and cracked the hash.
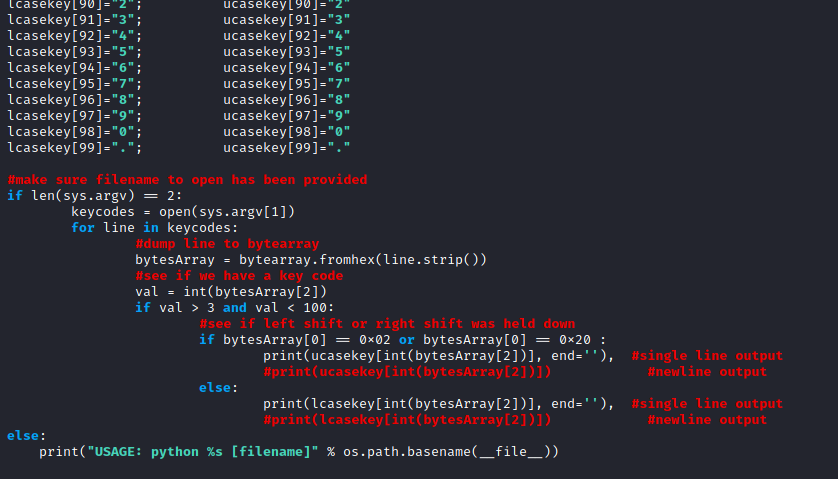
Recovering USB Raw Data from packet capture (.pcap) file.
The task was to extract raw USB data from wireshark.
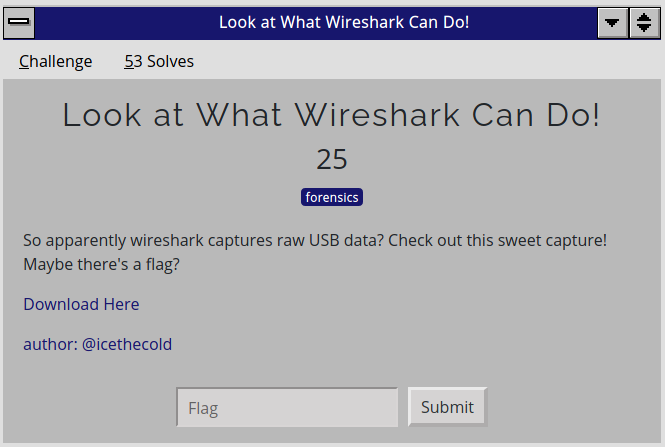
The downloaded file was a .pcap file that captured usb transfer data. What I was interested in were packets that contained data.
(usb.data_flag == "present (0)")
Also, the Info field indicating USB_INTERRUPT in intrigued me as it was likely a keystroke or some form of I/O.
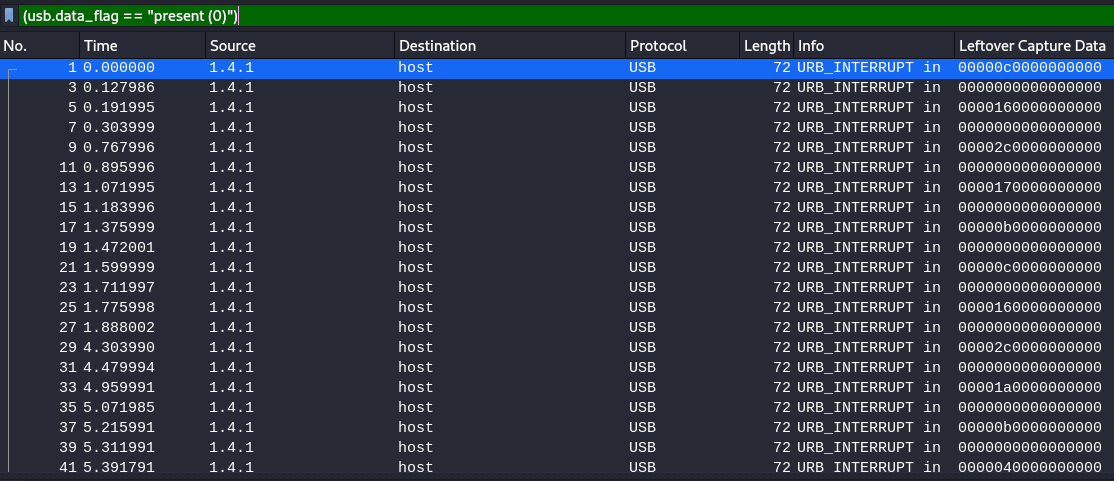
I enabled the Leftover Capture Data field as a column, because the value contains the raw USB data. However, I had to find a way to extract the values efficiently. And I found that tshark could do this.
tshark -r file.pcap -T fields -e usb.capdata
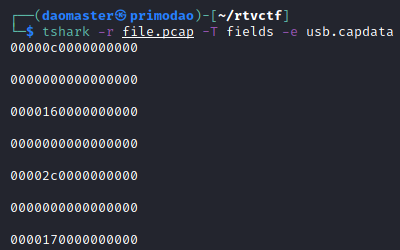
I looked up online and came across a similar scenario where the individual was trying to extract raw USB data.
Also it confirmed my suspicions that the USB_INTERRUPT in was indeed for keystrokes.
I successfully extracted the message using the script in the blogpost (credits to the author), which converts the Usage IDs into ASCII keystrokes.