This is a continuation from my previous post. These are the challenges recorded in this part 2 of 2 post:
- Network Forensics - Malware Capture
- Kevins Chili - Sweeper
- Sherlock Holmes QR Code Adventure - 1. & 2.
- Bonk Wallet - 0x01. dev bonk
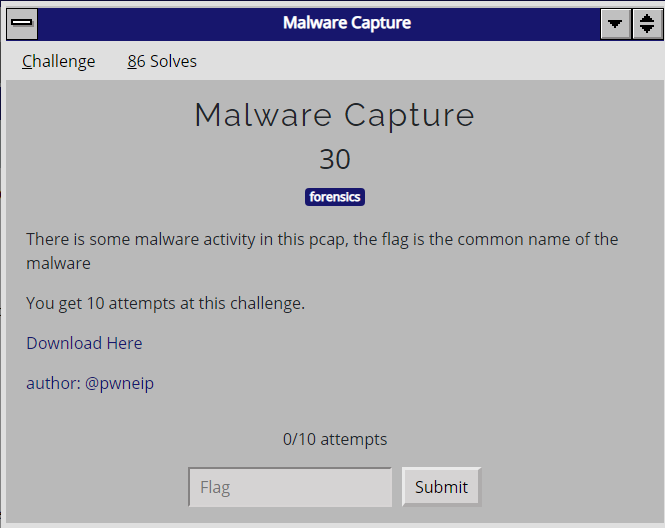
Malware Capture
For this challenge, I was given a pcap file named notmalware.pcap, with a malware network traffic. My goal was to identify the common name for this malware.
Usually, I would take records of the endpoint and network devices, to visualise the network topology. However, I skipped all of those and looked directly to files transferred during this capture.
There was no HTTP traffic, only SMB. So I used Wireshark's Export Objects > SMB, and found a peculiar file named Penguins.jpg.
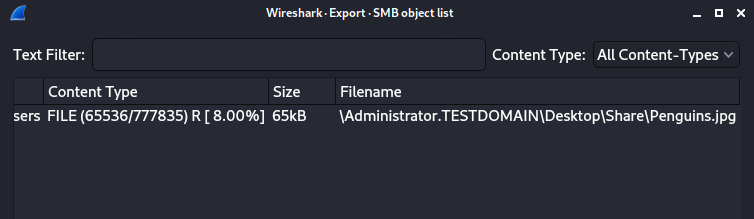
I downloaded the file and looked at its metadata, as I wasn't sure if it was hiding an actual malware. Running exiftool, I noticed some odd information such as Adobe.
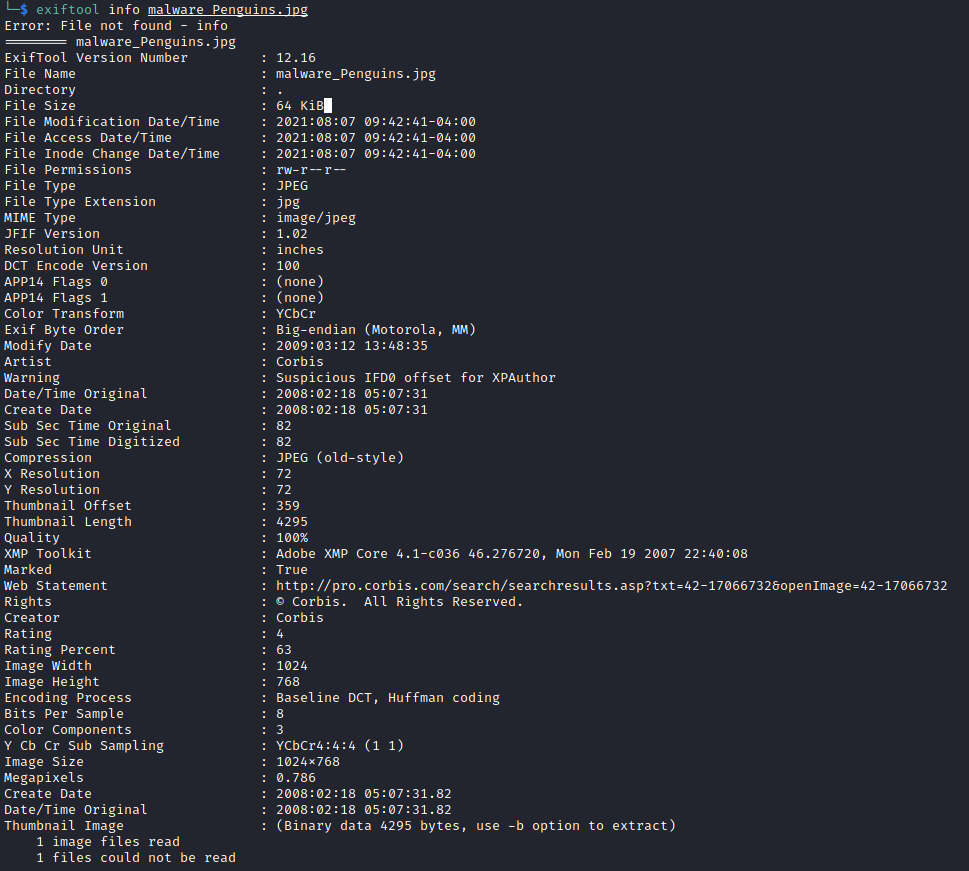
Next, I generated a MD5 hash of Penguins.jpg to see if I could get any info online.
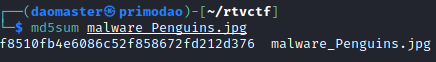
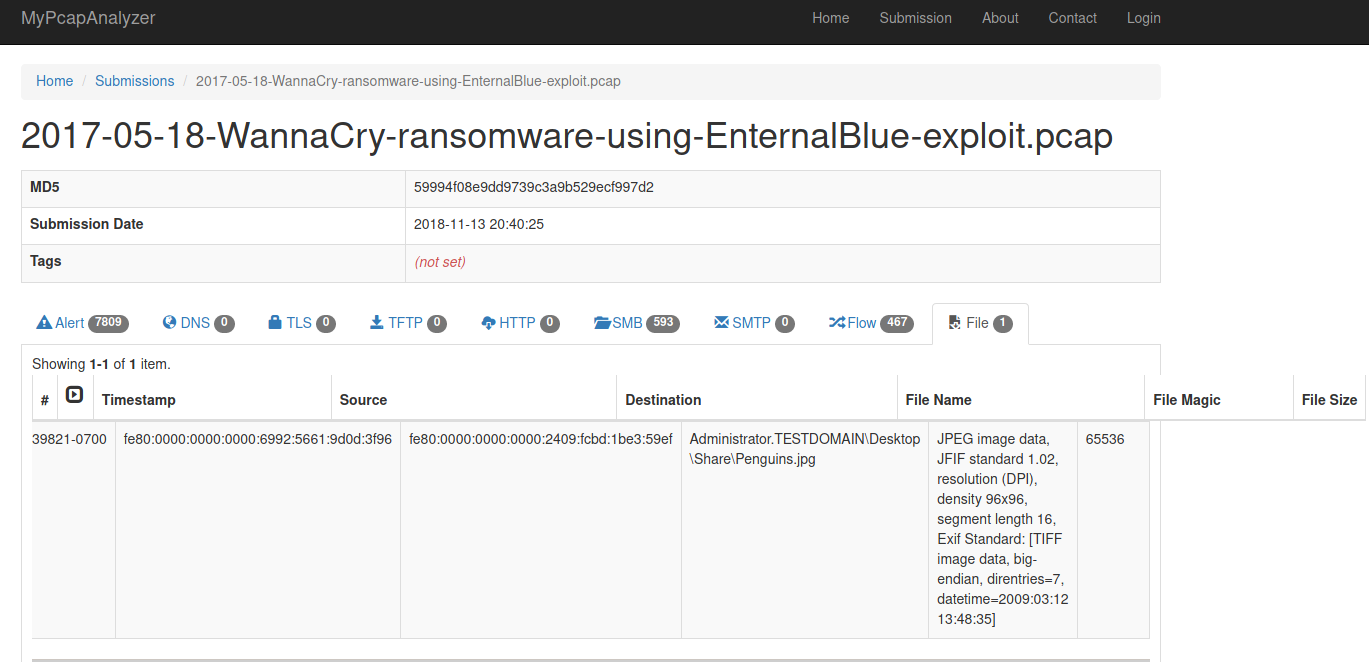
From my search, the results returned were very similar to what I was looking at. And the title gave it away, so I managed to score for this challenge. Flag: WannaCry
Kevins Chili - Sweeper
This challenge was really interesting, it was a continuation for another challenge Kevins Chili - Ingredient. There was a web version of minesweeper hidden in the website. And the game was impossible to beat by playing normally.
The minesweeper board was 20 x 20 and only 10 cells were safe. I knew there had to be some other way to beat the game, so I opened up the browser console and found a javascript that contained the main functions of the game.
I analysed the code and found the winning condition required to get a flag.
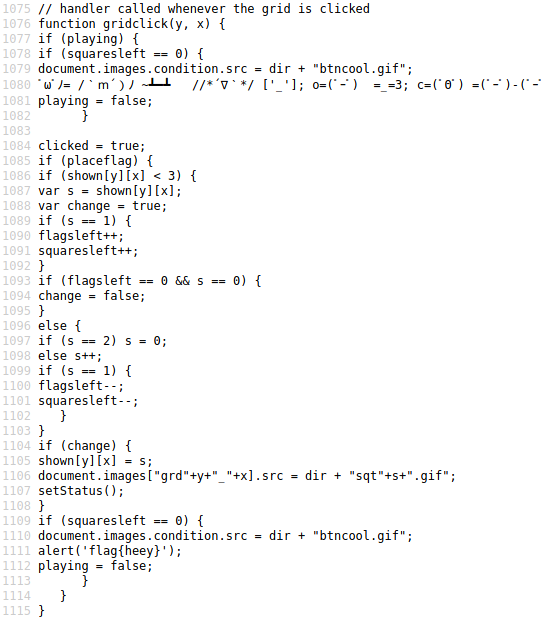
From the code, I understood that the safe cells were marked as False in a nested array. So I wrote a script to click on the cell with the gridclick() function if the element was False. The problem I faced was that the game did not end. This was because the game code did not reach the check at line 1109.
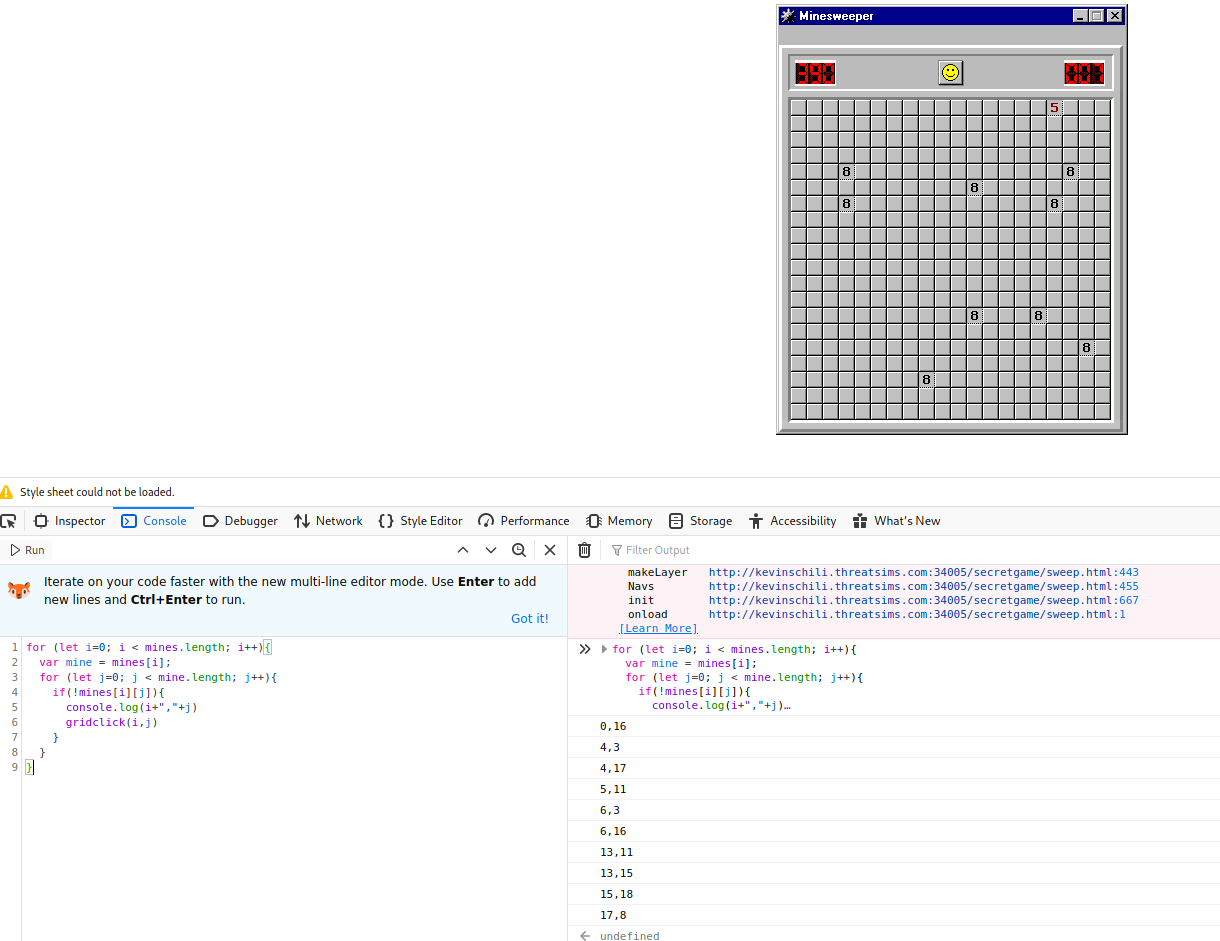
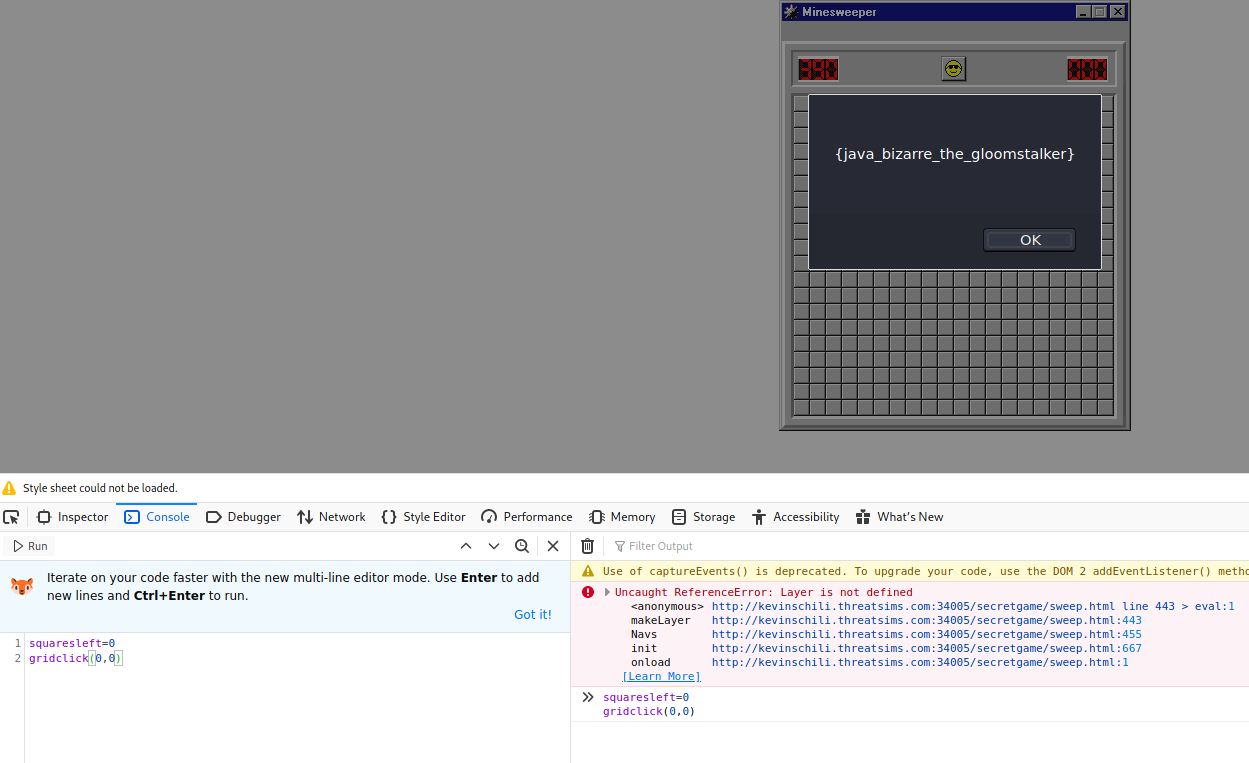
So I scraped the code and did a much simpler method. I set variable squaresleft = 0, and trigger the game to check the win condition by calling gridclick(). It does not matter if I selected a mine or not as the winning condition only checks if the squaresleft == 0.
Sherlock Holmes QR Code Adventure - 1. The Beginning
This was a 5-part steganography challenge, which I could only solve 1. I only went halfway into the 2nd challenge but however couldn't solve it.
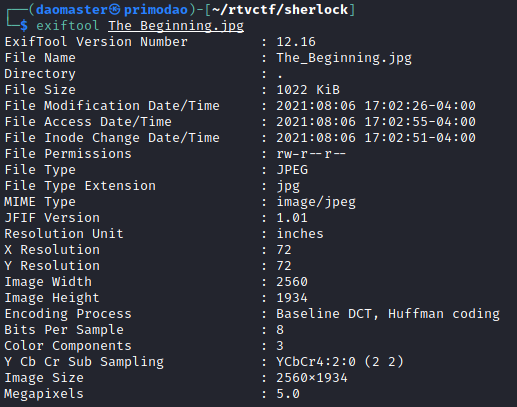
The file was an image file named The_Beginning.jpg. Knowing there must be a flag within, I ran exiftool to see if the flag was kept in the metadata.
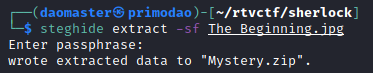
Nothing much I could tell from here, so I used steghide to try extracting any hidden files out.
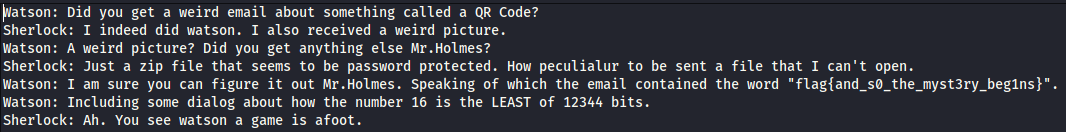
Steghide worked and extracted the file. Within there were a few things, a partial QR code and a note, which contained the flag.

Sherlock Holmes QR Code Adventure - 2. The Mismatched Picture
This was the second challenge which I did not complete.
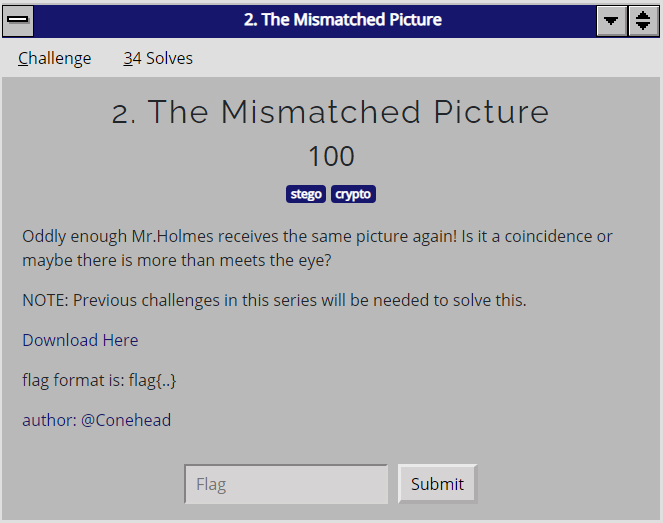
The image provided was a similar one to The_Beginning.jpg from the first challenge, however it was significantly larger in size. Steghide did not work this time, so I used an online decoder for it.
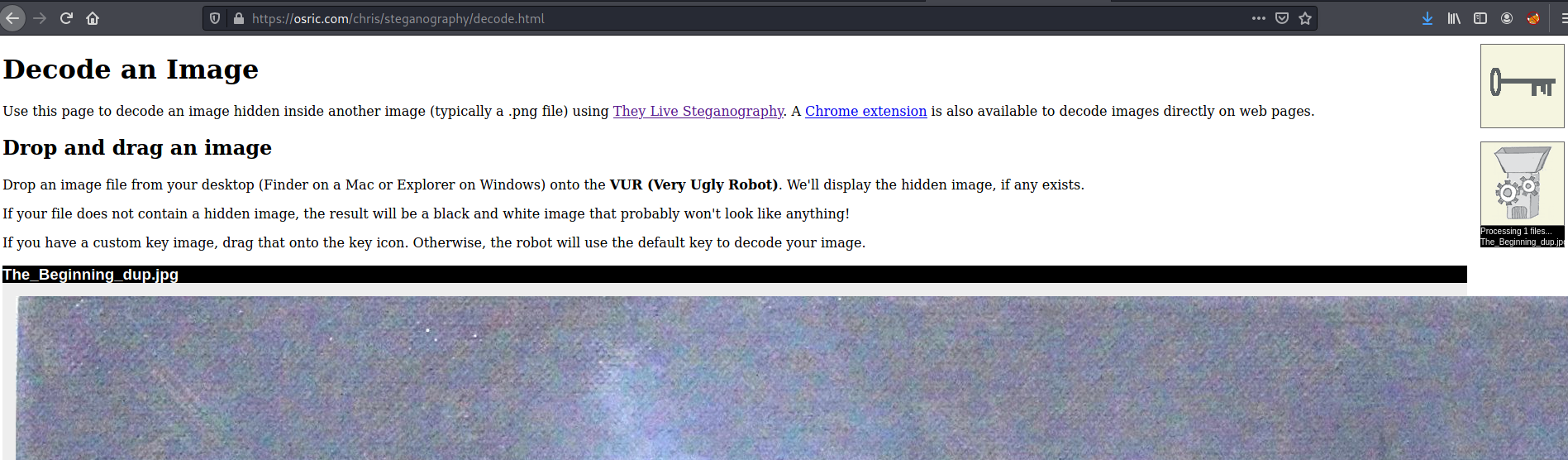
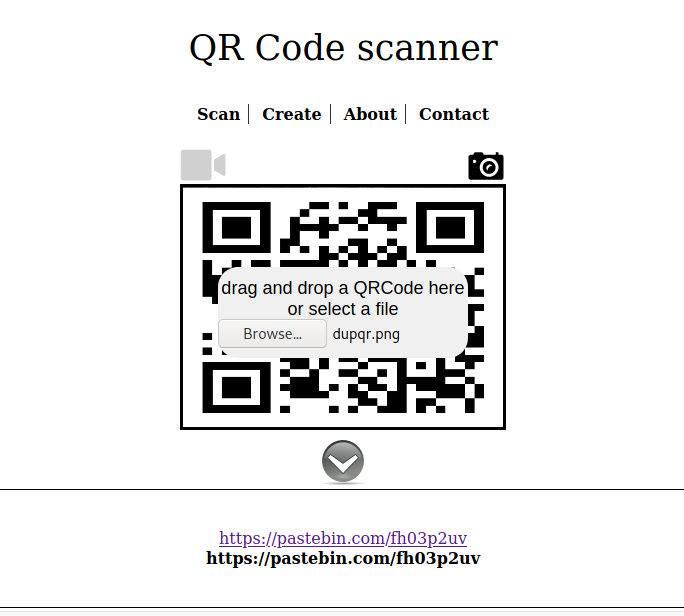
The online decoder managed to extract an underlying image inside The_Beginning_dup.jpg, and it was a QR Code. Reading the QR code, I was brought to a link on pastebin, which a list of strings were dumped. No flag there. I spent a little more time but no avail, so I moved on to another challenge.
Bonk Wallet - 0x01. dev bonk
This challenge was an interesting one, the first to a 4-part series challenge. This first challenge included the need to rely on OSINT to obtain credentials to a user's wallet.
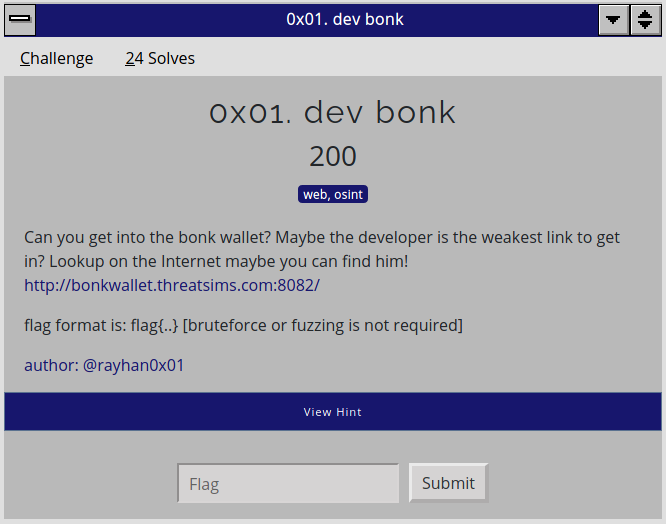
In the given URL, there was a web application that was about a cryptocurrency called bonk, and the task was to get into the developer's wallet. For this challenge, I used a hint (which cost me 10 points), and it hinted that the developer might have uploaded personal stuff onto GitHub.
This was what I found after a little digging in GitHub:
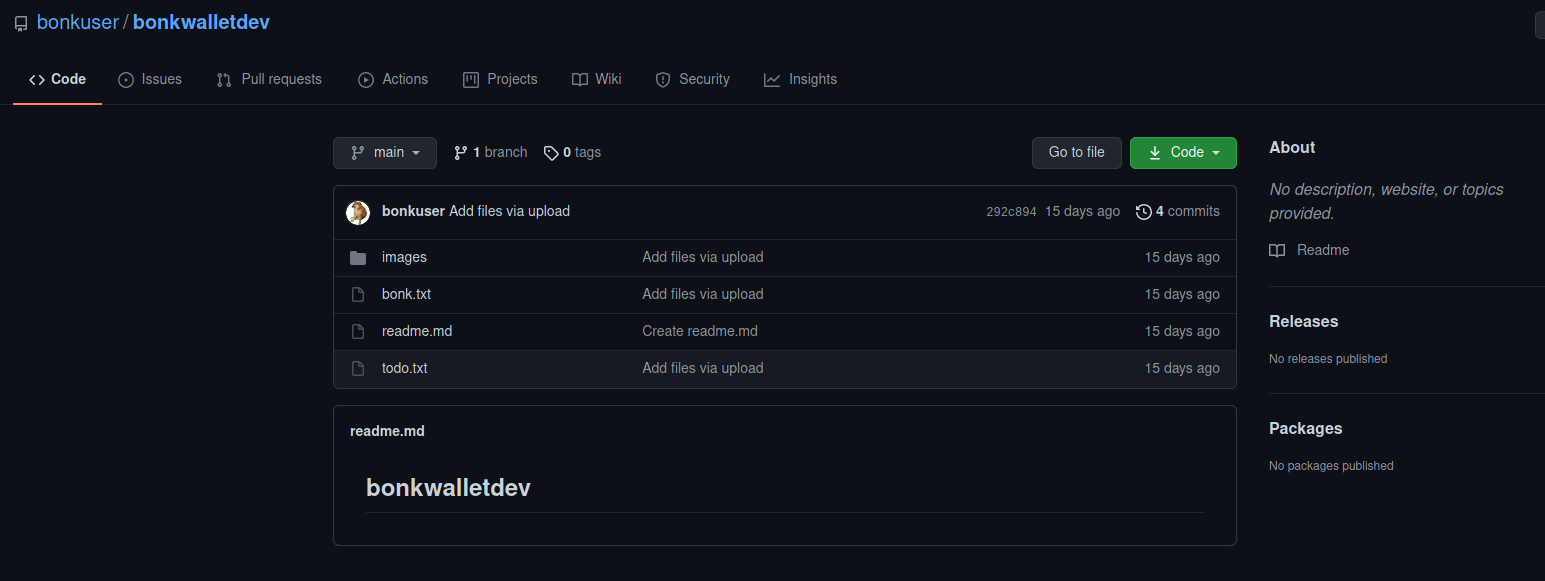
I scoured through the image folder and found a peculiar image.
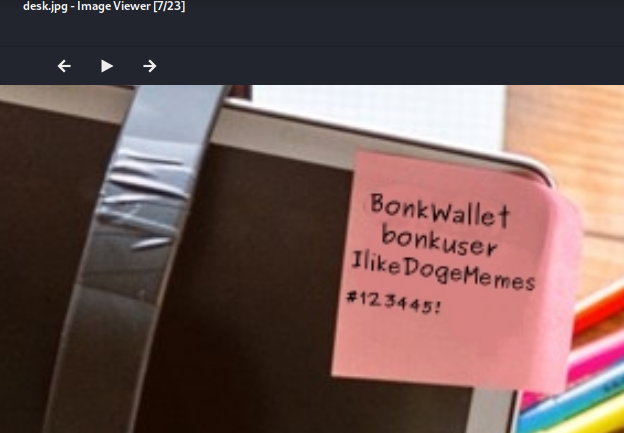
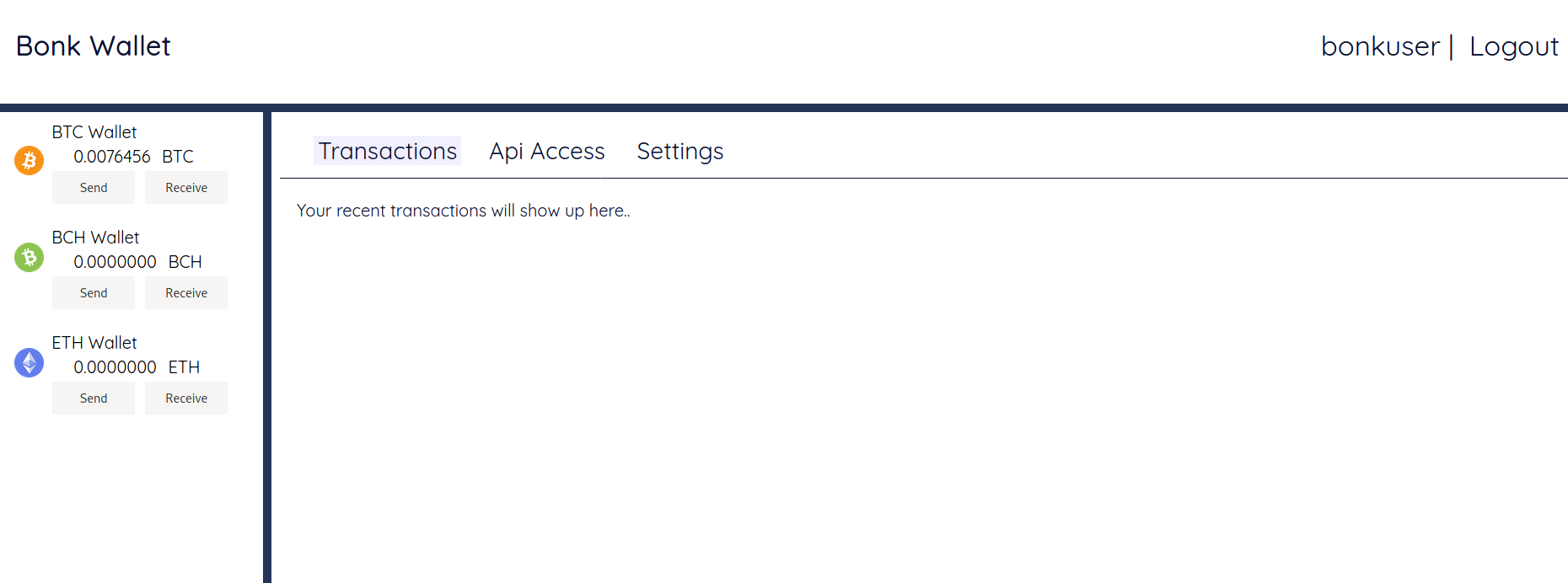
I got into bonkuser and the flag for this challenge was found in the Settings page.
Game Over
Unfortunately time ran out and I was not able to complete the next challenge, 0x02. richbonk.
Conclusion
My friends and I all had lots of fun participating in this event. Although we didn't make it into the qualifiers, we were happy with our progress and the things we learnt along the way. 10/10 would participate again.